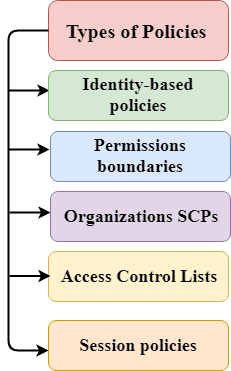
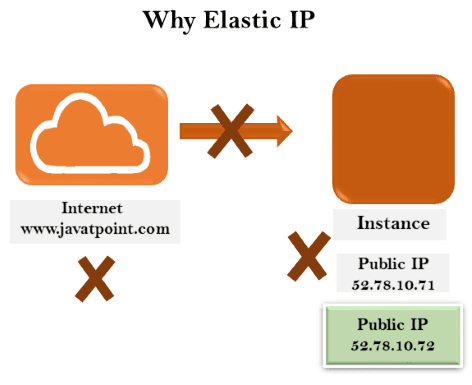
AWS Blog Info - Content
Content 1.Guide To Configure Amazon Web services-AWS Blog Info 2.What is Cloud Computing-AWS Blog Info 3.Introduction TO Amazon Web services-AWS Blog Info 4.Amazon web services -Basic Architecture-AWS Blog Info 5.Amazon web services Management Console-AWS Blog Info 6.Amazon web services Console mobile app-AWS Blog Info 7.How to create AWS Free Account-AWS Blog Info 8.Amazon EC2 (Elastic Compute Cloud)-Awsbloginfo 9.Auto Scaling-AWS Blog Info 10.Amazon WorkSpaces -AWS Blog Info 11.Amazon Web services(AWS) Lambda-Awsbloginfo 12.Amazon Virtual Private Cloud (VPC)-AWS Blog Info 13.Amazon Route 53-AWS Blog Info 14.AWS Direct Connect -Awsbloginfo 15.Amazon Elastic Block Store (EBS)-AWS Blog Info 16.Amazon S3 (Simple Storage Service)-AWS Blog Info 17.AWS Storage Gateway-AWS Blog Info 18.CloudFront(CDN)-AWS Blog Info 19.Am...